The US Department of Defense’s (DoD) Command, Control, Communication, Computers, Cyber, Intelligence, Surveillance and Reconnaissance (C5ISR) systems, are defined as “technology that enables networked soldiers to gain information dominance and decisive lethality”.1 These systems – which have been critical to our successes in maintaining the peace, fighting the war on terror, and enabling the defense of Ukraine – encompass network-connected devices ranging from satellites to laptops to night vision sensors. Our military and North Atlantic Treaty Organization allies are under an ever-increasing threat of cyber attacks from foreign adversaries and non-state actors intent on threatening our information dominance.
In June 2023, the Department of Defense (DoD,) several other Federal agencies, and NATO member countries suffered an attack targeting a vulnerability in a widely used software that companies use to move large files.2 An even larger attack in 2020, suspected to have been committed by a group backed by the Russian government, went undetected for several months and affected thousands of organizations. The attackers exploited software or credentials from at least three U.S. firms, including Microsoft, SolarWinds, and VMware.2
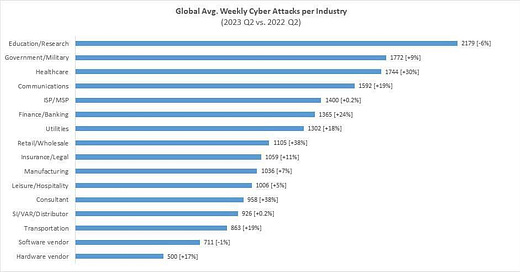
As seen in the chart below, these attacks are just the tip of the proverbial iceberg. The DoD and the security related education / research sector are the top 2 priorities for cyber attackers. The DoD, which arguably has the most to lose, experienced 1,772 attacks per week during Q2 20234, which was a 9% increase from the Q2 2022. The sheer number of attacks will prevent the DoD from being able to completely eliminate the mechanisms by which these infiltrations occur. However it doesn’t mean the DoD and other Federal agencies are defenseless.
Source: Checkpoint.com “Global Average Weekly Cyber Attacks per industry”
Let’s take a closer look at “advanced persistent threats” (APT’s), which includes man-in-the-middle (MITM) attacks, vulnerabilities in messaging apps, and third-party data-sharing. China, Russia, Iran, and North Korea are using these attacks to target DoD C5ISR systems, resulting in the loss of key intelligence, weapon-system intellectual property, and force-maneuverability information. Combined, it is not hyperbole to say the United States’ Information Dominance is in danger. As the DoD further rolls-out a strategy known as “Bring Your Own Device” (BYOD)6, which aims to allow, and sometimes require, its uniformed and civilian personnel to use their personal devices for work-related activities, the ability to protect sensitive information becomes even more challenging.
So in light of these APT’s the question becomes, how can the DoD operate not only safely, but also from a truly “information dominant” position necessary to ensure peace, in this challenging, ever-changing environment.
Cyber defense will require a collection of capabilities and systems. The private sector is innovating to provide them. One company - Cyphlens - has the opportunity to not only provide increased security, but also to enable a wholesale rethinking of intelligence classification and sharing. Cyphlens's mission is to create innovative solutions that protect agencies, enterprises, and consumers in everyday transactions with as minimal friction as possible. Cyphlens turns any mobile device into a powerful decryption device, providing a unique technology to encrypt and decrypt your mission-critical C5ISR information in a way that achieves the mission while greatly reducing the opportunity for compromise. Most cybersecurity defenses focus on stopping hackers and fraudsters at the login page. Cyphlens provides a second level of defense against the ones who break through.
With Cyphlens, accessing, viewing and sharing transactional data is secure and resilient against advanced targeted attacks and malware, by going beyond the traditional encryption (that is, encryption at rest, in transit, and in use) to create a fourth state - “data-in-view.” This includes visual representations of encrypted data, similar to but very different from commonly-used QR codes. At its core Cyphlens would enable the DoD to determine who could access sensitive data. However, it also enables greater control - where can the data be accessed, when can it be accessed, how many times can it be accessed, and how long can it be accessed.
Intrigued? Want to learn more about the solution? A brief video can be unlocked through this Ciphertext (make sure to take your phone off silent mode for audio). Download Cyphlens from the Apple store or Google Play to explore more.
Cyphlens is one of many start-ups attacking the Cyber security challenges. By tapping into cyber innovation across the United States, the DoD can take significant steps to maintaining C5ISR dominance to ideally prevent conflict - and in the event of conflict, ensure the victory of our military forces.
Still intrigued? Want to learn about use cases for the DoD? They can be unlocked through this Ciphertext.
_______________________________________
Sources
U.S. Army Combat Capabilities Development Command DEVCOM C5ISR Center | Article | The United States Army
Andres Tiray, June 16, 2023. Cyberattack impacts U.S. federal government, NATO allies. Here's what we know about the breach so far. - CBS News
VMware Flaw a Vector in SolarWinds Breach?". Krebs on Security. (December 7, 2020). Menn, Joseph (December 18, 2020). "Microsoft says it found malicious software in its systems"
https://dodcio.defense.gov/Portals/0/Documents/Library/DoD-ZTStrategy.pdf (11/22/22)
https://dodcio.defense.gov/Portals/0/Documents/Library/UseOfNon-GovernmentOwnedMobileDevices.pdf (8/10/22)